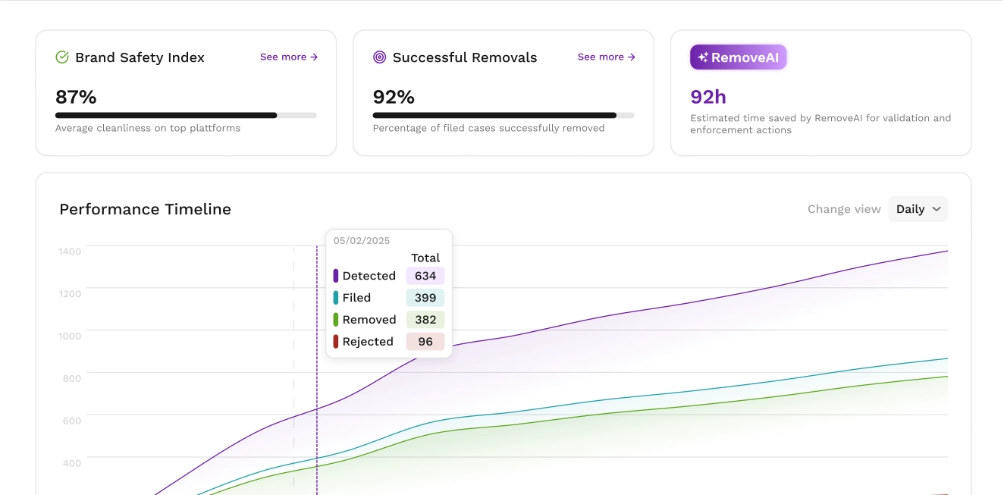
In today’s digital landscape, online content spreads fast—and so do violations. Whether you’re dealing with copyright infringement, phishing pages, malware hosting, defamation, or brand impersonation, knowing how to submit effective hosting provider takedown requests is essential. A poorly written or misdirected request can be ignored, delayed, or rejected, allowing harmful content to remain live longer than necessary. As soon as one fake website is removed, a new site often appears, creating a 'whack-a-mole' effect for security teams.
What Is a Hosting Provider Takedown Request?
A hosting provider takedown request is a formal notice sent to a web hosting company asking them to remove or disable access to specific content hosted on their servers. Hosting providers are often obligated—by law or by their own terms of service—to act on valid requests involving illegal or policy-violating content.
Common legal frameworks include:
- DMCA (Digital Millennium Copyright Act) for copyright infringement
- Defamation and harassment laws
- Privacy and data protection regulations
- Terms of Service (ToS) violations
Hosting providers typically act faster than website owners, making them an effective escalation path.
Introduction to Takedown Requests
- A takedown request is a formal process to remove infringing or malicious content from the internet, often involving hosting providers and domain registrars.
- The goal of a takedown request is to protect against phishing attacks, brand impersonation, and other cyber threats. Distinguishing between legitimate and fraudulent sites is crucial for effective takedown requests.
- Understanding the takedown process is crucial for effective brand protection and combating phishing sites. Customer reports are often the first indication of malicious activity, helping to detect threats early.
- Hosting providers play a significant role in the takedown process, and it’s essential to know how to report abuse and submit takedown requests. DMCA takedowns are reactive tools and cannot prevent initial compromises from phishing and impersonation scams. Phishing sites can harvest hundreds of victims within hours of going live, making rapid takedown action essential.
When Should You File a Takedown Request?
You should consider a hosting provider takedown request when content is:
- Copyright-infringing (pirated media, copied text, stolen images)
- Defamatory or false statements harming reputation
- Privacy-violating (doxxing, leaked personal information)
- Malicious or harmful (malware, phishing, scams)
- In violation of the host’s acceptable use policy
If contacting the website owner directly has failed—or is unsafe—going to the hosting provider is often the next best step.
Step-by-Step: How Hosting Provider Takedown Requests Work
1. Identify the Hosting Provider
Use tools like WHOIS lookup or IP address scanners to determine where the site is hosted. Accurate identification is crucial—sending a request to the wrong provider delays action.
2. Gather Clear Evidence
Successful takedown requests rely on solid documentation:
- URLs of the offending content
- Screenshots or archived copies
- Proof of ownership (for copyright claims)
- Clear explanation of the violation
The clearer your evidence, the faster the response.
3. Reference the Correct Legal or Policy Basis
Specify why the content must be removed:
- DMCA violation
- Defamation
- Privacy breach
- Terms of Service violation
Hosting providers are far more responsive when requests align with recognized legal or policy obligations.
4. Submit the Request Properly
Most hosting providers have:
- Dedicated abuse email addresses
- Online abuse reporting forms
- DMCA-specific submission portals
Always follow their preferred process to avoid rejection.
Best Strategies for Effective Takedown Requests
1. Be Precise and Professional
Avoid emotional language or threats. Hosting providers respond best to:
- Clear facts
- Specific URLs
- Neutral, professional tone
This improves credibility and speeds up review.
2. Cite Policies and Laws Explicitly
Referencing exact clauses from:
- DMCA
- Hosting provider ToS
- Applicable local laws
demonstrates seriousness and reduces back-and-forth.
3. Prioritize the Most Harmful Content
If multiple pages are involved, focus on:
- The main URLs causing harm
- Index pages or files hosting multiple violations
This can lead to broader removals with less effort.
4. Keep Records of All Communication
Maintain a log of:
- Submission dates
- Responses
- Case numbers
This is essential if you need to escalate or pursue legal action later.
Common Mistakes to Avoid
- Sending vague requests without URLs or evidence
- Targeting the wrong entity (e.g., domain registrar instead of host)
- Overstating claims without legal backing
- Ignoring counter-notice procedures in DMCA cases
Mistakes can delay takedowns or even expose you to legal risk.
What If the Hosting Provider Doesn’t Respond?
If a host is unresponsive, consider escalation:
- Contact the upstream provider or data center
- Notify the domain registrar
- File complaints with relevant authorities
- Seek legal counsel for persistent violations
In many cases, layered escalation leads to faster results.
Proactive Takedown Prevention Strategies
Beyond reacting, consider proactive measures:
- Regularly monitor your brand, content, and IP
- Register copyrights where applicable
- Use automated brand protection tools
- Maintain template takedown notices for quick response
Preparation reduces response time when issues arise.
Understanding Phishing and Brand Impersonation
- Phishing sites and fake websites are used by threat actors and malicious actors to trick users into revealing sensitive information or installing malware. These sites are often part of broader phishing activities and phishing scams orchestrated to impersonate legitimate brands and deceive users.
- Brand impersonation involves the use of malicious domains, impersonation attempts, or social media profiles to deceive customers and damage a brand’s reputation. Impersonation attempts frequently involve the creation of lookalike domains and phishing emails to deceive users.
- Phishing attacks can be devastating, resulting in financial loss, reputational damage, and compromised customer data. Phishing domains are designed to impersonate legitimate websites, tricking users into disclosing sensitive information.
- Combatting phishing requires a proactive approach, including continuous monitoring, threat intelligence, and effective takedown strategies. Cybercriminals often create batches of lookalike domains, making the takedown process more complex.
- Proactive domain risk monitoring is essential for detecting impersonation attempts and suspicious activity before significant harm occurs.
DMCA Takedown Notice
- A DMCA notice is a formal legal tool used to report copyright infringement and domain abuse under the Digital Millennium Copyright Act.
- The notice must include detailed evidence, such as URLs, screenshots, and proof of ownership or copyright. A valid DMCA takedown notice must specifically list the URLs of the infringing material and include a statement of good-faith belief.
- Hosting providers and domain registrars are required to respond to DMCA takedown notices and remove infringing content. DMCA notices also require proof of ownership or control over the original content to be valid.
- Once a DMCA notice is accepted, the infringing content is usually removed within a few business days.
- However, the DMCA takedown process can be slow, and phishing sites can continue to operate during this time, highlighting the need for additional takedown strategies. DMCA takedowns are reactive tools for IP infringement and are not proactive defenses against fraud. Phishing sites can harvest hundreds of victims within hours of going live, making DMCA takedowns ineffective against them. Fraudsters often launch multiple lookalike domains after a DMCA takedown, making it difficult to eliminate the threat. The DMCA takedown process can also be time-consuming and complex, especially when dealing with multiple domains. Additionally, DMCA enforcement is inconsistent outside the U.S., reducing its effectiveness globally.
Takedown Strategies for Phishing Sites
- Effective takedown strategies involve a combination of manual and automated processes, including reporting abuse, submitting takedown requests, and using threat intelligence. Key features of automated takedown services include real-time detection of phishing domains and rapid response to emerging threats.
- Social media platforms, app stores, and domain registrars must be notified of phishing sites and fake content. Modern takedown platforms automate the detection and removal of phishing sites across multiple digital environments, helping to prevent user access to malicious content and attacks.
- Takedown workflows should be streamlined and efficient to minimize the time phishing sites remain active. These services can initiate takedowns in as little as 60 seconds and often include real-time alerts and evidence collection to support takedown requests.
- Proactive measures, such as continuous monitoring and website code analysis, can help prevent phishing attacks and brand impersonation. Automated takedown initiation coordinates in-house workflows and evidence packaging to fast-track the removal of detected phishing and spoofed domains.
- Manual takedown processes are time-consuming and complex, with each takedown requiring its own investigation, evidence gathering, and follow-up.
Identifying and reporting suspicious URLs is a critical step in the takedown process, as it helps prevent user access to malicious content and attacks.
Hosting Provider Takedown Requests
- The host (hosting provider) is responsible for taking action against sites involved in phishing and fraud, including those hosting fake login pages to steal data.
- It is important to keep your own website secure to prevent it from being exploited or abused by malicious actors.
- Hosting providers must respond to takedown requests and remove infringing content, including phishing sites and malicious domains.
- Providers automatically act to take down sites infected with malware or involved in phishing to protect server security.
- The takedown process may involve multiple stakeholders, including domain registrars, network providers, and law enforcement.
- Hosting providers take down websites based on formal abuse reports like DMCA notices, which provide clear evidence of terms of service violations.
- Under the Digital Millennium Copyright Act (DMCA), hosting providers must act expeditiously to remove or disable access to allegedly infringing content to maintain safe harbor protection.
- Hosting providers follow a structured procedure to take sites offline, which includes evidence gathering, notification, temporary suspension, and potentially permanent termination.
- Hosting providers verify abuse reports by checking the evidence against their Acceptable Use Policy and legal requirements before taking action.
- Failure to comply with hosting service requirements can lead to account termination and reputational damage for website owners.
- If a customer fails to comply with a violation notice, the hosting provider may suspend or terminate their service.
- Clear communication and detailed evidence are crucial for successful takedown requests.
Domain Takedowns
- Domain takedowns involve the removal of malicious domains or URLs used for phishing or brand impersonation.
- Domain registrars play a significant role in the domain takedown process, and it’s essential to know how to report abuse and submit takedown requests.
- Domain takedowns can be complex, involving multiple stakeholders and jurisdictions.
- Effective domain takedown strategies require a deep understanding of the domain registration process and the role of domain registrars.
Abuse Reports and Phish Reports
- Abuse reports and phish reports are essential tools for reporting suspicious URLs and phishing sites. A phish report is a specialized service for reporting phishing sites, offering features like real-time detection, automated evidence collection, and integration tools to help organizations identify and eliminate phishing websites efficiently.
- These reports should include detailed evidence, such as URLs, screenshots, and proof of ownership or copyright. When submitting a report to the abuse contact, it is important to include as much detail as possible to support your claim.
- Abuse reports and phish reports can be submitted to hosting providers, domain registrars, and social media platforms.
- Clear and concise reporting is crucial for effective takedown requests and minimizing the time phishing sites remain active.
Tips for a Strong Abuse Report
Submitting a well-crafted abuse report to a hosting provider or domain registrar can make all the difference in how quickly malicious domains or phishing sites are taken down. To maximize the effectiveness of your abuse reports, follow these best practices:
- Be precise with URLs: Always include the exact URL of the phishing site or malicious domain. This helps the hosting provider or registrar quickly locate and assess the problematic content.
- Provide detailed evidence: Attach screenshots, email headers, or relevant logs that clearly demonstrate the abuse. The more concrete your evidence, the easier it is for the provider to take action.
- Specify the type of abuse: Clearly state whether the issue is phishing, malware, copyright infringement, or another form of abuse. This ensures your report is routed to the correct team for swift handling.
- Keep it concise and focused: Stick to the facts and avoid unnecessary details. A focused report is easier for the provider to process and act upon.
- Follow up if needed: If you don’t receive a response within the provider’s stated timeframe, send a polite follow-up to check on the status of your report.
- Leverage specialized services: Consider using tools like ThreatWatch360, which can help you detect malicious domains, gather detailed evidence, and generate pre-filled abuse reports for faster submission.
By following these tips, you can help ensure that your abuse reports are taken seriously and that phishing, malicious domains, and other threats are addressed promptly by the hosting provider or registrar.
Social Media Takedowns
- Social media takedowns involve the removal of fake social media profiles or content used for phishing or brand impersonation.
- Social media platforms have dedicated processes for reporting abuse and submitting takedown requests.
- Social media takedowns require a deep understanding of each platform’s policies and procedures.
- Effective social media takedown strategies involve a combination of manual and automated processes, including reporting abuse and using threat intelligence.
Brand Protection Strategies
Protecting your brand from phishing attacks, fake websites, and malicious domains requires a proactive and multi-layered approach. Here are key strategies to strengthen your brand protection efforts:
- Monitor your digital footprint: Regularly scan the internet for phishing sites, lookalike domains, and fake websites that could be impersonating your brand. Early detection is crucial for rapid response.
- Leverage threat intelligence: Stay ahead of emerging threats by utilizing threat intelligence feeds and monitoring for new phishing kits or tactics used by cyber criminals.
- Establish a robust takedown process: Develop clear internal workflows for reporting abuse and submitting takedown requests to hosting providers, domain registrars, and other relevant platforms.
- Build strong partnerships: Collaborate with hosting providers and domain registrars to ensure your takedown requests are prioritized and handled efficiently.
- Educate your customers: Provide guidance on how to recognize phishing attacks and encourage them to report suspicious activity. Informed customers are your first line of defense.
- Consider professional brand protection services: Solutions like ZeroFox offer comprehensive monitoring, threat intelligence, and takedown support to help keep your brand protected across the internet.
By implementing these strategies, you can better combat phishing, reduce the risk of brand impersonation, and ensure your customers remain safe from emerging threats.
Comprehensive Takedown Use Cases
- Comprehensive takedown use cases involve a range of scenarios, including phishing attacks, brand impersonation, and malicious content.
- Takedown strategies must be tailored to each use case, taking into account the specific threats and stakeholders involved.
- Effective takedown use cases require a deep understanding of the threat landscape and the role of hosting providers, domain registrars, and social media platforms.
- Continuous monitoring and threat intelligence are essential for identifying emerging threats and developing effective takedown strategies.
Future of Takedown Requests
The landscape of takedown requests is rapidly evolving as technology and cyber threats advance. Here’s what the future holds for combating phishing sites, malicious domains, and infringing content:
- Increased automation: Artificial intelligence (AI) and machine learning (ML) will streamline the detection and reporting of abuse, enabling faster identification and removal of phishing sites and malicious domains.
- Seamless integration with platforms: Takedown processes will become more integrated with social media platforms, app stores, and search engines, allowing for quicker action against infringing or malicious online content.
- Blockchain for verification: Blockchain technology may be used to verify the authenticity and ownership of online content, making it harder for threat actors to distribute fake sites or infringing material.
- Proactive monitoring and intelligence: Continuous monitoring and advanced threat intelligence will become standard, helping organizations stay ahead of emerging threats and phishing attacks.
- Evolving legal frameworks: The Digital Millennium Copyright Act (DMCA) and similar regulations will adapt to address new types of cyber attacks and online abuse, improving the takedown process for all stakeholders.
- Enhanced collaboration: As cyber attacks grow more sophisticated, cooperation between hosting providers, domain registrars, brand owners, and security teams will be essential for effective takedowns and improved online safety.
Staying informed about these trends and adopting a proactive approach will help organizations remain resilient against phishing, abuse, and other digital threats in the years to come.
Fake Websites: What They Are and How to Take Them Down
Fake websites are deceptive sites designed to impersonate legitimate businesses, brands, or individuals. They are commonly used for scams, phishing, spreading malware, or damaging reputations. These sites often look convincing, making them especially dangerous for users who don’t notice subtle warning signs.
Common Types of Fake Websites
- Phishing sites pretending to be banks, login pages, or online services
- Brand impersonation sites using copied logos, layouts, and content
- Scam stores advertising fake products or unrealistic discounts
- Clone websites duplicating legitimate sites to mislead visitors
Warning Signs of a Fake Website
- Misspelled or suspicious domain names
- No contact information or fake addresses
- Poor grammar or low-quality design
- Requests for sensitive information (passwords, payment details)
- No HTTPS or invalid security certificates
How to Report and Remove Fake Websites
- Identify the hosting provider using IP or WHOIS lookup tools
- Collect evidence, including URLs, screenshots, and copied content
- Submit an abuse or impersonation report to the hosting provider
- Report the site to the domain registrar if the host is unresponsive
- Notify search engines to reduce visibility and prevent harm
Best Strategy for Fake Website Takedowns
Hosting providers take fake websites seriously—especially those involved in fraud or phishing. Clearly explain how the site violates their Acceptable Use Policy, provide proof of impersonation, and request immediate suspension to protect users.
Phishing Websites: Identification, Risks, and Takedown Strategies
Phishing websites are fraudulent sites created to trick users into revealing sensitive information such as login credentials, financial details, or personal data. These sites often impersonate trusted brands, services, or institutions and are one of the most common and dangerous online threats today.
How Phishing Websites Work
Phishing sites typically:
- Mimic legitimate login pages or checkout screens
- Use copied branding, logos, and layouts
- Send victims through email, SMS, or social media links
- Collect entered data and transmit it to attackers
Because of their direct threat to users, phishing websites are treated as high-priority abuse cases by hosting providers.
Common Signs of a Phishing Website
- URLs that closely resemble legitimate domains
- Urgent messages encouraging immediate action
- Requests for passwords, OTPs, or payment details
- Poor grammar or subtle design inconsistencies
- Recently registered or suspicious domains
How to Take Down a Phishing Website
1. Identify the Hosting Provider
Use IP lookup or WHOIS tools to determine the hosting company responsible for serving the site content.
2. Gather Strong Evidence
Include:
- The phishing URL(s)
- Screenshots of the fake pages
- Proof of brand impersonation (if applicable)
- Any emails or messages directing users to the site
3. Submit an Abuse Report
Most hosting providers have a dedicated abuse or phishing report channel. Clearly state that the site is engaging in phishing and poses an immediate risk to users.
4. Escalate if Necessary
If the host is slow to respond:
- Contact the domain registrar
- Report to upstream providers
- Notify browsers or security services to flag the site
Best Practices for Phishing Website Takedowns
- Act quickly—phishing sites are often short-lived
- Use clear, factual language and avoid speculation
- Reference the host’s Acceptable Use Policy
- Prioritize user safety in your request
Hosting providers often suspend phishing sites within hours when presented with credible evidence.
Preventing Future Phishing Threats
- Monitor for domain lookalikes of your brand
- Educate users on safe browsing habits
- Register common typo domains
- Set up automated phishing detection alerts
Infringing Content: How to Identify It and Get It Removed
Infringing content refers to material published online without proper authorization, violating intellectual property rights such as copyrights, trademarks, or proprietary ownership. This type of content can cause financial loss, brand damage, and legal complications if not addressed quickly.
Common Types of Infringing Content
- Copyright infringement (copied articles, images, videos, music)
- Trademark infringement (unauthorized use of brand names or logos)
- Pirated software or digital products
- Stolen designs, templates, or source code
- Unauthorized resale of protected content
How to Identify Infringing Content
You may be dealing with infringement if:
- Your original content appears elsewhere without permission
- Logos or trademarks are used to mislead users
- Paid or licensed material is distributed for free
- Content is slightly modified to avoid detection
Documentation of ownership is critical for successful takedowns.
How to Remove Infringing Content
1. Confirm Your Ownership
Ensure you have clear proof such as:
- Original files or publication dates
- Copyright registration (if available)
- Trademark certificates or licensing agreements
2. Locate the Hosting Provider
Use WHOIS or IP tools to identify the host responsible for the infringing material.
3. Submit a Formal Takedown Request
For copyright violations, submit a DMCA takedown notice. For trademark infringement, reference the host’s Acceptable Use Policy and provide proof of brand ownership.
4. Monitor for Re-Uploads
Infringing content is often reposted. Ongoing monitoring helps prevent repeat abuse.
Best Practices for Infringing Content Takedowns
- Provide exact URLs of infringing material
- Clearly differentiate original vs infringing content
- Keep communication factual and professional
- Track responses and deadlines carefully
What If the Host Rejects the Request?
If a hosting provider denies the takedown:
- Review and strengthen your evidence
- Escalate to the domain registrar
- Report to search engines for deindexing
- Seek legal advice for persistent infringement
Preventing Future Infringement
- Use copyright notices and watermarks
- Monitor the web for stolen content
- Register trademarks and copyrights
- Maintain ready-to-use takedown templates
Final Thoughts
Hosting provider takedown requests are one of the most effective tools for removing harmful or illegal online content—when done correctly. By understanding the process, using strong evidence, and applying strategic communication, you significantly improve your chances of swift action.
Whether you’re protecting intellectual property, safeguarding personal information, or defending your reputation, a well-crafted takedown strategy ensures you stay in control in an increasingly complex online world.
FAQs
1. What is the difference between a hosting provider and a domain registrar?
A hosting provider stores and serves website content on its servers, while a domain registrar manages the website’s domain name. For content removal, hosting providers are usually the correct party to contact because they control the actual data being displayed.
2. How long does it take for a hosting provider to process a takedown request?
Response times vary, but many hosting providers review valid takedown requests within 24 to 72 hours. Urgent cases involving malware, phishing, or severe policy violations may be handled more quickly.
3. Can a hosting provider refuse a takedown request?
Yes. A hosting provider may reject a request if it lacks sufficient evidence, does not violate their policies, or fails to meet legal requirements (such as an incomplete DMCA notice). Providing clear documentation improves approval chances.
4. Do I need a lawyer to submit a hosting provider takedown request?
In most cases, no. Many takedown requests—especially DMCA or policy-based complaints—can be submitted without legal representation. However, legal advice may be helpful for complex defamation or international cases.
5. What happens if the website owner files a counter-notice?
If a valid counter-notice is submitted (common in DMCA cases), the hosting provider may restore the content unless legal action is taken within a specified timeframe. Understanding counter-notice procedures is essential before filing a takedown request.